
Cloud Security Assessment
Cloud Security Assessment
With the increasing popularity of cloud services, attackers are also focusing specifically on these services. Hackers are targeting managed cloud service providers and their customers and exploiting vulnerabilities. When companies use cloud technologies, they must also ensure that they are secure.
At this point, you should think about a cloud security assessment. terreActive offers two options for this, the cloud penetration test and the configuration review.
What is the cloud penetration test?
Cloud computing is the provision of IT resources via the internet on a pay-as-you-go basis. This allows you to access a variety of technology services such as computing power, storage space and databases instead of buying, owning and maintaining physical data centers and servers.
Cloud penetration tests are attack simulations that are performed to find vulnerabilities that hackers could exploit or to identify misconfigurations in a cloud-based system. With cloud penetration tests, companies get to know the strengths and weaknesses of their cloud system in order to subsequently improve their security measures.
As the name suggests, the configuration review focuses on the configuration itself and its stability.
What type of assessment do you need?
This depends on which cloud model you have chosen.
If you use cloud services, part of your infrastructure is managed directly by an external cloud provider, who is also partly responsible for security. Cloud providers, especially the large and well-known ones, invest a lot of money in security to protect the infrastructure. For this reason, the penetration test focuses primarily on finding vulnerabilities in the parts of the stack that are your responsibility. With the IaaS model, there are many more.
Cloud models. What is the customer's responsibility?
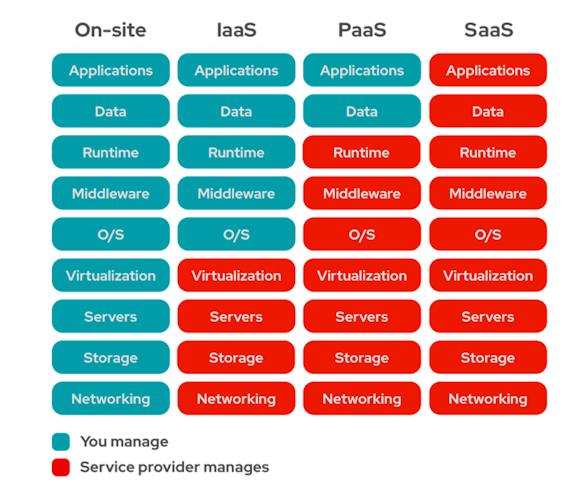
It all depends on which cloud model you want to test:
- Infrastructure-as-a-Service (IaaS), such as AWS or MS Azure. Here we recommend a cloud penetration test.
- Platform-as-a-Service (PaaS), such as Heroku, Windows Azure or AWS Beanstalk.
- Software-as-a-Service (SaaS), i.e. a tenant in a finished application, such as SalesForce or DropBox. A configuration review is recommended here, as most areas are the responsibility of the cloud provider.
Penetration test or configuration review?
Although the two types of cloud security assessments are similar, they have some key differences.
In a configuration review, the auditor has read access to all or part of the cloud account that they need to check. He examines the configuration of the services (S3, IAM, Cloud SQL etc.) for stability and robustness, which gives you insight into your cloud and thus helps you to configure it securely.
In a cloud penetration test, the tester starts with no or limited access when testing a «breach-assumed» scenario - for example, assuming that an attacker has compromised a server in the cloud or a specific user. They will then attempt to escalate their privileges to reach other parts of the cloud environment and access sensitive data.
In a configuration review, the tester will not have the same overview of the cloud environment, and although they will likely try to break down the cloud configuration, it will not be reviewed in the same way. The tester will try to link the vulnerabilities found or gather information from outside the environment that might be helpful. This approach gives a better idea of what an attacker could do from a certain perspective.
The cloud penetration test generally uncovers a number of vulnerabilities that need to be remedied in the next step. However, as you will also receive a list of recommendations with measures together with the test results, you will quickly be able to improve your security setup.
Not quite sure what you need? Contact us and together we will find the right solution for you.
